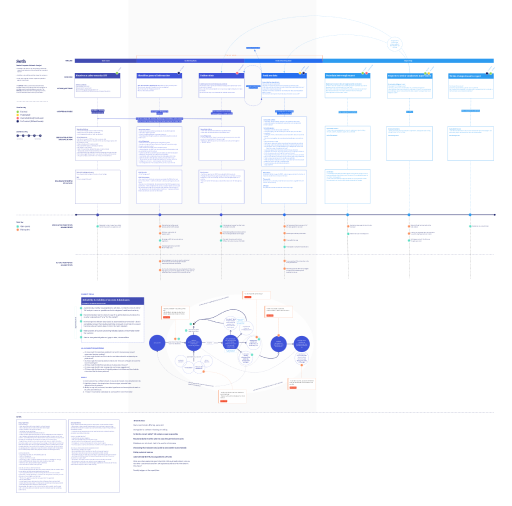
A Day in the Life of a Junior Computer Network Analyst
Responding to RFI: Seth receives cyber security request for information (RFI) throughout his day. These RFIs may arrive at any time, via email or chat, and are typically based on Seth's individual expertise.
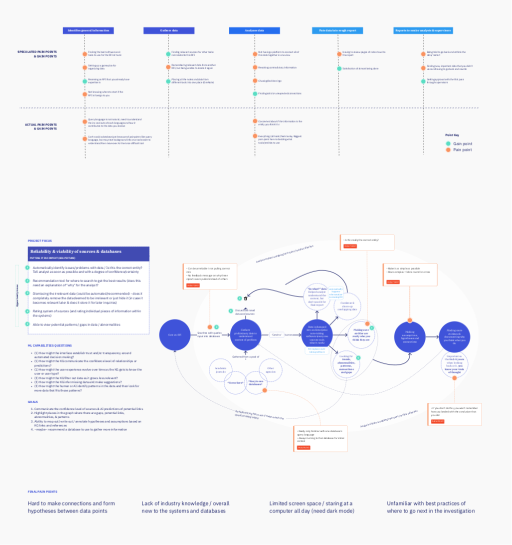
Information Identification: Seth's initial task is to identify general information about the RFI. He is familiar with general topic areas but need to gather context to understand the specifics. He reaches out to coworkers for insights and consults internal databases such as academic journals, reports from other agencies, and avoids using low-rated sources.
Data Collection and Consolidation: Seth gathers relevant data for each RFI and consolidates it in a central location where everyone can see the information.
Data Analysis: As Seth collects data, he continuously analyzes it to identify trends, abnormalities, and connections. And he strives to keep his analysis simple and easy to understand.
Reporting: Seth creates a rough report and sends it to senior analysts and supervisors for review. After receiving feedback, he writes a comprehensive report that addresses the original RFI, ensuring that the information provided is both accurate and relevant to the request at hand.
*The official language of Kobia (a fictitious foreign nation), also referring to the people and culture of the nation.

 Cyber/Computer Network Analyst (CNA)
Cyber/Computer Network Analyst (CNA)